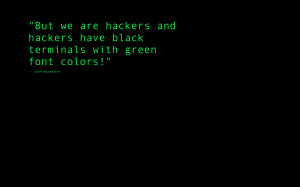
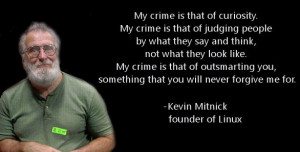
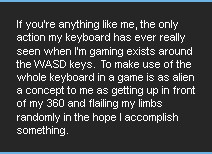
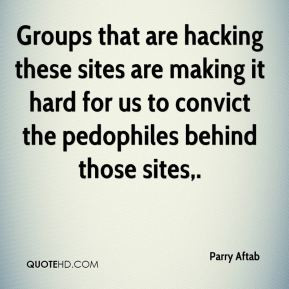
Hackers Quotes
For countries such as Kenya to emerge as economic powerhouses, they need better infrastructure: roads, ports, smart grids and power plants. Infrastructure is expensive, and takes a long time to build. In the meantime, hackers are building 'grassroots infrastructure,' using the mobile-phone system to build solutions that are ready for market.